Earlier this month, Microsoft threat analysts released an alert in a blog post warning organisations of a new attack vector being used to deploy malware.
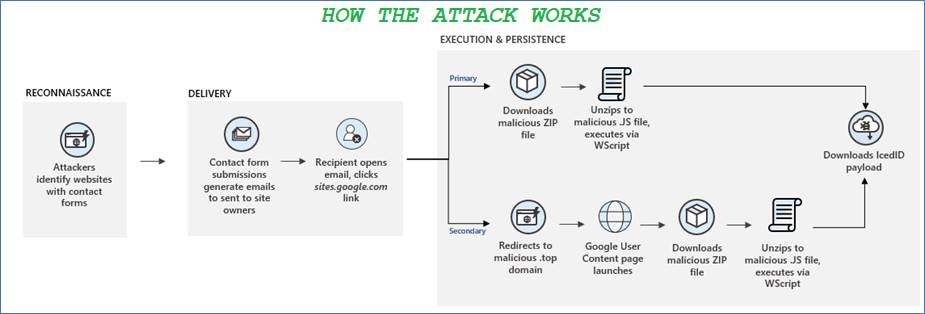
Earlier this month, Microsoft threat analysts released an alert in a blog post warning organisations of a new attack vector being used to deploy malware.

With 2020 coming to an end, after what felt like an eternity to many, cybersecurity & technology firm CrowdStrike have released their annual ‘Cyber Front Lines’ incident-analysis report, and it contains much food for thought. One of the more striking figures is that more than half of the cyber attacks they investigated involved ransomware; a form of malware which encrypts any files it can find until a ‘ransom’ is paid. Ransomware attacks are known to be extremely destructive, spreading quickly through networks and shutting down critical operations as they go.
Financially-motivated attacks in general, the majority of which were ransomware-based, made up 63% of the more than 200 incidents they responded to, demonstrating that the file-encrypting malware is big business for cyber criminals, and not going away any time soon.

These are undoubtedly strange times we are living in, with unprecedented changes taking place in our lives all over the globe in order to fight the pandemic that is Covid19. Suddenly, a sizeable chunk of the workforce is working from home, in many cases for the first time. Companies are scrambling to put in place plans to accommodate this, working out whether to allow users to use their own devices, or provide company laptops or desktops for any displaced staff. Moreover, many people are out of work altogether and confined to their homes, spending significantly more time than usual browsing the internet, looking for the next clue online that will bring some certainty to their lives around the crisis they are living through.
With such a shift in online activity comes great challenges for technology companies and IT teams in ensuring their users are safe and their precious company data is secure – meanwhile cyber criminals have seen crisis as opportunity; the misfortune of others is a chance for them to take advantage of the confusion and make some extra money.

The Covid19 pandemic is the perfect storm for cyber criminals to up the ante. Confusion reigns among users and misinformation is rife. Users who would normally be at work are now accessing the internet from home devices, which typically are not sitting behind the advanced firewalls, email filters and policies put in place by their organisations to protect them against malicious activity.
Read moreA strain of ransomware titled SamSam has earned its handlers over 5.1 million euros to date, according to estimates, since it first began hitting enterprises in 2015. Security firm Sophos has released the data in a report, after tracking the Bitcoin addresses found on SamSam ransom notes and sample files.
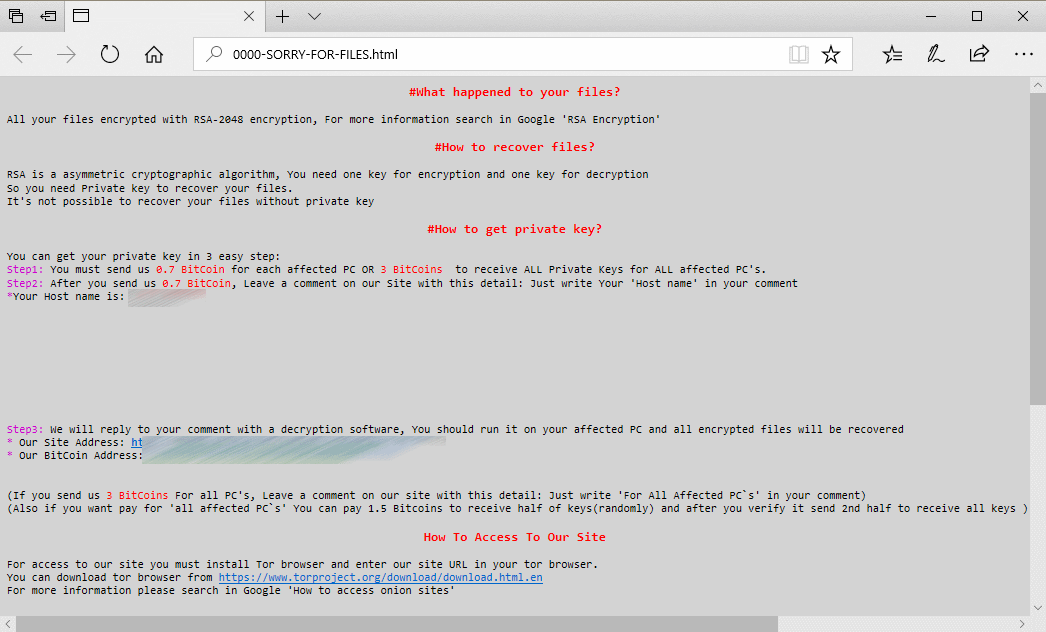
It seems that everyone in the cyber security sphere is talking about ransomware these days. Last year, attacks such as WannaCry, NotPetya and BadRabbit took the business world by storm, costing billions in damages. Ransomware is by no means a new threat (it has been around since at least 2005), but it is one of the fastest growing and most costly. Cyber crime is constantly changing, and criminals keep creating news ways to steal money. Ransomware has gotten increasingly sophisticated since 2005, but the people using and deploying it haven’t necessarily – now some cyber criminals are making more money selling high-tech ransomware strains to non-technical criminals than if they were to conduct the attacks themselves. The result is that more and more ‘hackers’ have access to ransomware and need very little technical know-how to operate it, leading to more and more ransomware attacks each year. It may come as a surprise, then, to hear that the FBI received less reports of ransomware attacks in 2017 than in 2016 and 2015, despite the increase in attacks.
