Have you been hit by ransomware recently? According to a recent survey by CyberEdge, the most reliable approach (by far) to defending against ransomware is proactive rather than reactive. That is to say, having a robust backup and disaster recovery system in place is far more likely to result in minimal disruption and data loss than trying to pay the criminals in the hopes that they do the ‘honourable’ thing and decrypt your critical data. For the report, CyberEdge surveyed IT security professionals and found that more than half (55%) had been hit by ransomware in 2017. The study found that of those who had prepared for ransomware using backups and other business continuity procedures, 86.9% were able to successfully recover their data. However, of those who didn’t have backups to rely on and instead paid the ransom, only 49% actually had their data decrypted and recovered.
As GDPR Looms – Cyber Criminals Move Towards Business Extortion
Trend Micro, one of the largest cyber security firms in the world, has released their annual security roundup report, and the results show some alarming trends. With the GDPR upcoming, cyber criminals have been refining their techniques in order to increase their financial gains, moving away from exploit kits which can be an unpredictable earner, to more reliable tactics such as business email compromise, phishing and spam, ransomware, and the relatively new threat to businesses, malicious crypto-currency mining.

Exploits kits are down, but 2017 saw over 300 new ransomware families, in addition to a rise in business email compromise scams and the all-new malicious crypto-mining threat.
US & UK Blame Russia for NotPetya, Most Costly Cyber Attack to Date
The governments of the UK, US, Australia and more have publicly blamed Russia for the NotPetya ransomware attacks, which crippled businesses all over Europe back in June 2017 with a particularly nasty and destructive strain of ransomware. Last Thursday, the White House press secretary Sarah Sanders stated that NotPetya was “a reckless and indiscriminate cyber-attack that will be met with international consequences”, squarely blaming the Russuan Military and the Kremlin for causing billions of dollars’ worth of damage to businesses and states alike. The same day, the British defence secretary Gavin Williamson accused the Russian government of “undermining democracy”, after the attack, which was primarily aimed at the Ukraine, spread uncontrolled throughout Europe and beyond and caused major disruption to commerce and public services.
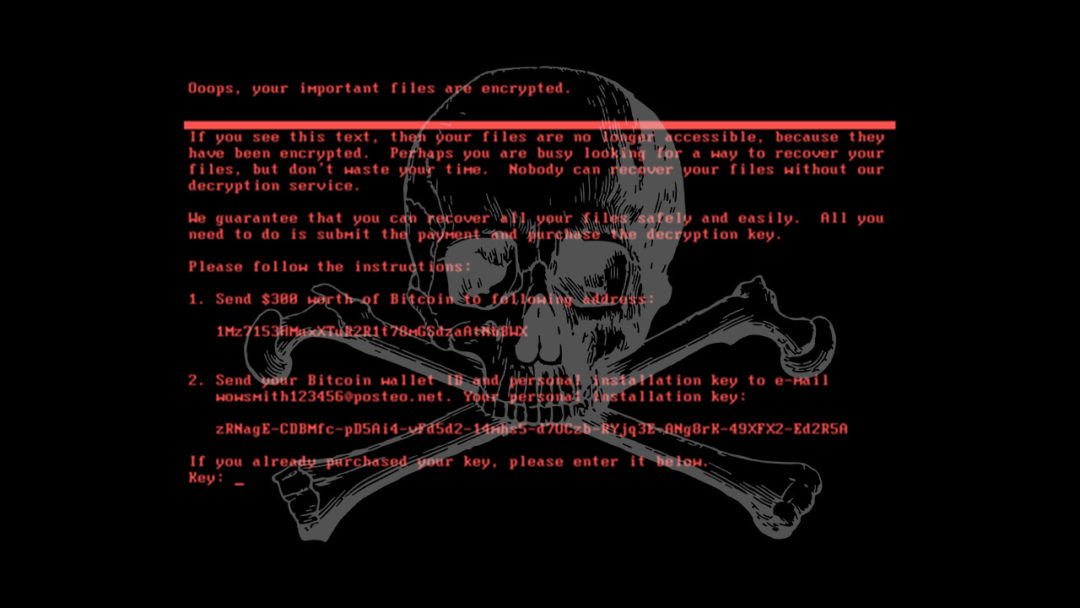
NotPetya has been described as a destructive political move disguised as a normal criminal attack seeking financial gain.
Macro Malware: A Common Weapon for Phishing Attacks
A macro is a small piece of code that runs within a software program such as Microsoft Word or Excel, and is normally used to automate common or repetitive tasks. Macro malware is the practice of hiding a virus in a macro code and enticing unsuspecting users into downloading a Word or Excel file and running the macro script within, which then will download a virus, malware or even ransomware onto that person’s PC. Macro malware was common during the 1990s, but lapsed in popularity through most of the 21st century as increasingly savvy PC users learned how to spot the spam or phishing emails that delivered them, which were often riddled with typos. Nowadays, however, macro malware is seeing a big return due to two factors – Phishing emails are becoming increasingly sophisticated and no longer have obvious typos in them, and ransomware – a very profitable form of malware for criminals – can be easily downloaded via a macro, leading to entire networks being encrypted and held to ransom. It is now critical that all users understand the threats that macro malware can pose, particularly to their organisation, and learn how to spot the attacks before it’s too late.
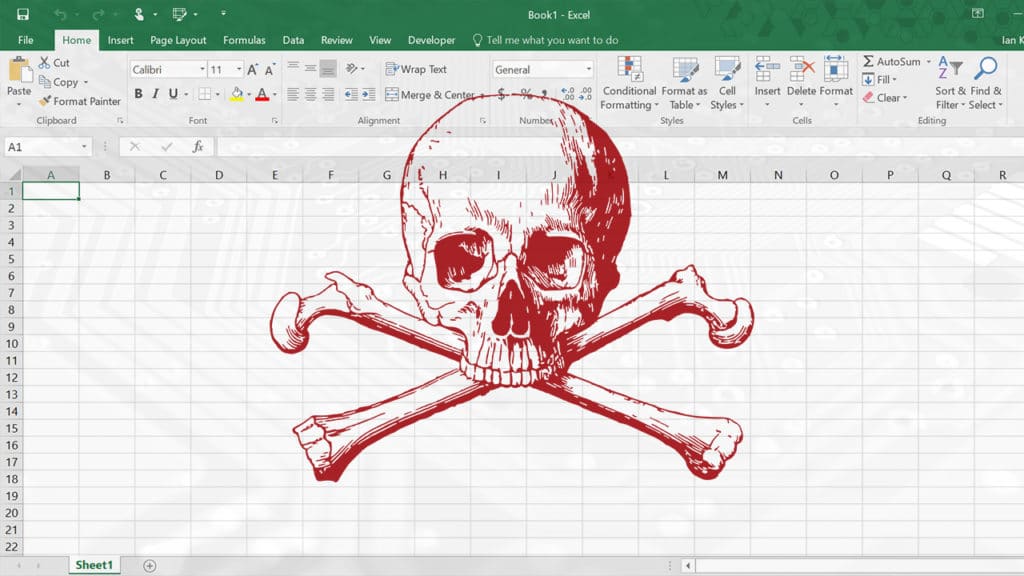
Excel files are a common means of transmission for macro malware, which can download ransomware to infect entire networks at a time
Cyber Security Is Not Just for IT – It’s for Everyone
Traditionally, cyber security has been seen as an IT department’s problem. They make sure everyone has antivirus on their PCs and take care of the firewall – and as long as they’re doing it right, then everyone else is safe… right? This has lulled users and business owners into a false sense of security of late, believing that cyber security simply isn’t their area or that it’s not in their job description. However, this attitude is now being taken advantage of in a big way by cyber criminals, who have discovered that individual users are much easier to target and deceive. As a result, users often takes actions which inadvertently allows the hackers to bypass the IT security systems. Traditional antivirus is dead, and even more advanced next-generation antivirus simply can’t stop the most deadly attacks. Now, everyone in an organisation has a part to play in keeping it secure, from the bottom all the way up to the CEO.


