Earlier this month, Microsoft threat analysts released an alert in a blog post warning organisations of a new attack vector being used to deploy malware.
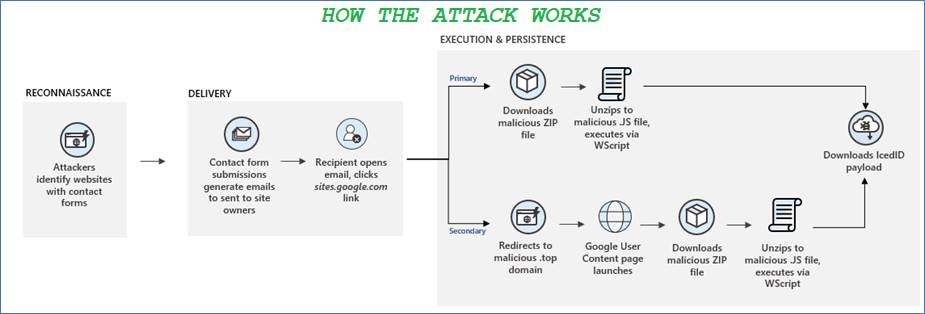
In order to bypass email filters and lend credibility to their phishing attacks, cyber criminals have been submitting their bogus emails via website contact forms.
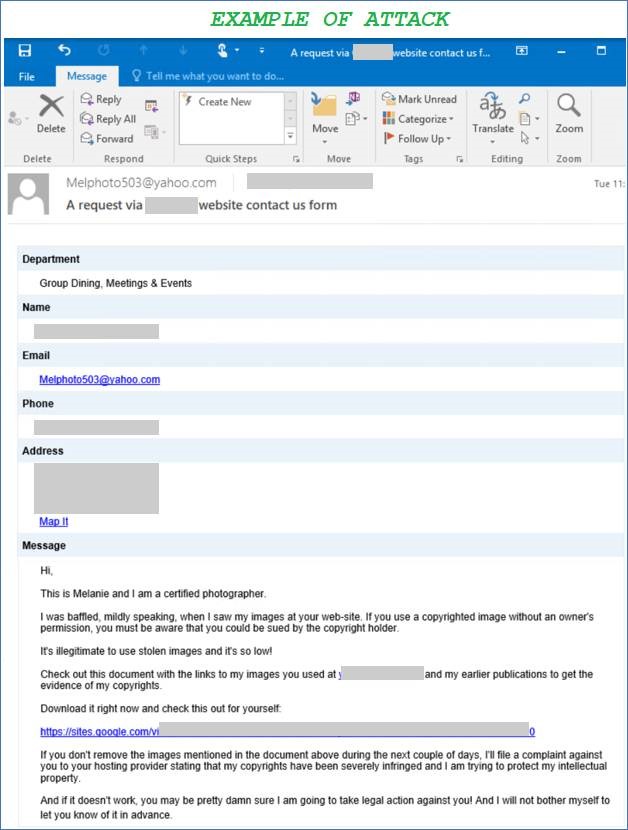
Like most phishing attacks, the emails utilise social engineering to try and trick users into opening a link. The emails make fake legal threats, usually relating to copyright infrigement (see example email at the bottom of this post) and request that the user reviews the alleged infractions on a third-party website.
Of course, once the user clicks the link, they automatically download a zip file containing IcedID malware, which infects their PC and steals their info. This malware was first seen back in 2017, and has been found to contain ransomware and other malicious payloads in addition to stealing sensitive data from unsuspecting victims.
Cyber criminals are constantly evolving and trying new attack vectors to breach organisation’s networks. Often, emails from website contact forms will be whitelisted within an organisation’s email environment, meaning the malware-laden emails are more likely to be delivered straight to the inbox of their intended recipient.
What’s more, the link itself is a genuine Google link and requires authentication to an Google account in order to supposedly view the offending content, which adds an extra layer to obfuscate the attack and bypass security systems. IcedID is not the only form of malware that can be delivered via this attack either; it all depends on the intended goal of the hackers.
Due to the fact that this attack vector can deliver emails straight to user inboxes using links that appear legitimate, it is easy to see how people can be caught out by it. This is just another example of how cyber criminals cleverly use social engineering to trick users into taking actions that will harm them and their organisation, and underlines the need for comprehensive security awareness training to help staff identify the red flags present at each step of the attack.
See below an example of what this attack looks like in the wild: