A strain of ransomware titled SamSam has earned its handlers over 5.1 million euros to date, according to estimates, since it first began hitting enterprises in 2015. Security firm Sophos has released the data in a report, after tracking the Bitcoin addresses found on SamSam ransom notes and sample files.
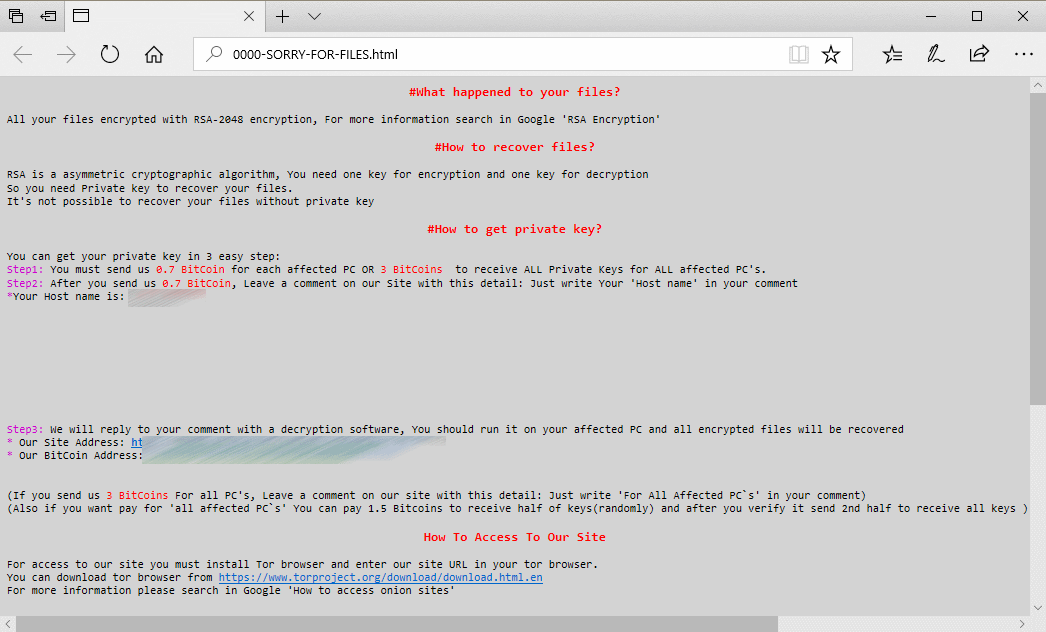
The note displayed on PCs that were infected by SamSam ransomware, as seen by businesses, hospitals, schools, local councils and more
Sophos has reported that most of the ransomware’s victims (74%) were based in the US, however other regions such as Canada, the UK, the Middle East and more were also affected by the SamSam strain. It focused mostly on larger enterprises, and as such affected organisations including schools, hospitals, and local councils.
“Many victims found that they could not recover sufficiently or quickly enough to ensure business continuity on their own, and reluctantly paid the ransom,” Sophos said.
“We believe there may be hundreds more victims who have made no public statement, but we don’t know who they are,” said Sophos researchers, adding that many victims reluctantly paid ransoms of up to $64,000 each, based on analysis of ransom payments to the bitcoin wallets tracked.
Victims of SamSam find that their PCs are encrypted and will not boot to allow them to access any of their files – instead a ransom note is displayed, urging them to pay Bitcoin into the criminals wallet or their files will be permanently erased.
Ransomware attacks such as WannaCry, NotPetya and BadRabbit ravaged European businesses last year, and the consequences are only set to become more grave now that the GDPR is in force. Under the GDPR, users have a right to access their data, and the company must oblige them by providing the user with any data they hold on them. However, companies who have been hit with a ransomware attack and are unable to restore said data would then be unable to provide this data to users, putting them in non-compliance with the GDPR.
Unlike most ransomware attacks, which tend to utilise phishing and spear-phishing to compromise an organisation, SamSam is surprisingly manual and executed step-by-step by a person, allowing the attackers to employ counter-measures and remain undetected in a network.
SamSam is a particularly thorough encryption tool, according to Sophos, rendering not only work data files unusable, but also the configuration and data files required to run applications, most of which are not routinely backed up.
The hackers gain access to a single compromised machine on the network first, before scanning for other vulnerabilities and installing their malicious code on critical machines. Then, they wait until the middle of the night to execute the main attack – encryption of the organisations PCs and servers.
The only sure defense against ransomware is having a robust, regularly-tested backup and recovery system and process in place, as cyber criminals and their techniques are constantly evolving to exploit new vulnerabilities and sneak past even complex security measures. Having backups to fall back on means that when (not if) a ransomware infection should occur, you have the ability to restore your data and get your business back up and running fast. Speak to us today to inquire about our managed backup service for businesses.
