Earlier this month, Microsoft threat analysts released an alert in a blog post warning organisations of a new attack vector being used to deploy malware.
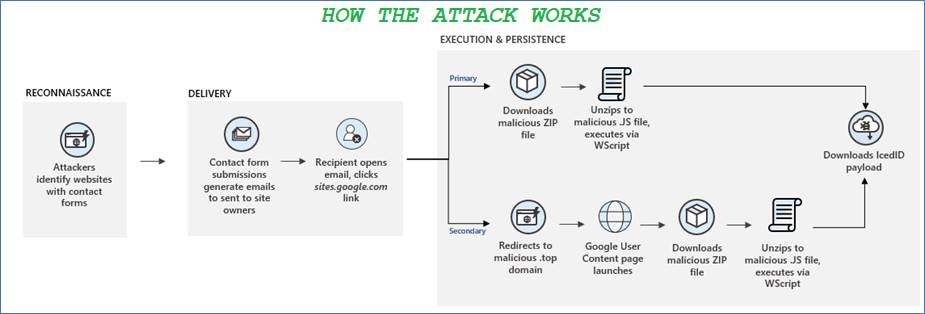
Earlier this month, Microsoft threat analysts released an alert in a blog post warning organisations of a new attack vector being used to deploy malware.

With 2020 coming to an end, after what felt like an eternity to many, cybersecurity & technology firm CrowdStrike have released their annual ‘Cyber Front Lines’ incident-analysis report, and it contains much food for thought. One of the more striking figures is that more than half of the cyber attacks they investigated involved ransomware; a form of malware which encrypts any files it can find until a ‘ransom’ is paid. Ransomware attacks are known to be extremely destructive, spreading quickly through networks and shutting down critical operations as they go.
Financially-motivated attacks in general, the majority of which were ransomware-based, made up 63% of the more than 200 incidents they responded to, demonstrating that the file-encrypting malware is big business for cyber criminals, and not going away any time soon.

Every year, the number of phishing scams seems to be increasing, with the malware-ridden emails getting continually more sophisticated and convincing. The latest global phishing campaign purporting to be from international courier giants DHL has been tricking users into opening a fake PDF attachment – and subsequently unleashed a previously unseen piece of malware to wreak havoc on their PCs.

Cyber criminals have always targeted users, finding it easier to trick unsuspecting employees than to bypass complex technical security measures – and this trend has been growing steadily the last few years. Identify fraud, where criminals impersonate someone else in order to steal their money or use their account to manipulate others, is now one of the most common types of cyber crime there is. Account takeover attacks, where criminals gain access to a user’s account and use it to send spam or phishing emails, is also on the rise, often allowing malicious emails to bypass email security filters.

Adobe has been forced to release an out-of-schedule emergency security patch to its users, after a zero-day vulnerability was discovered to affect Adobe Flash Player. Users are being urged by Adobe to update to version 30.0.0.113 of Flash Player, which contains mitigations for the zero-day as well as addressing three other flaws. This latest flaw was discovered already being used in the wild to attack Windows users, and doesn’t exploit browsers like typical Flash exploits – instead, it works through Microsoft Office documents which it utilises to download and execute malicious code.
