Why Learning How to Spot a Phish Is Important
Despite constant improvements in cyber-security, the manipulation of users who fail to spot a phishing email remains the criminals’ best option for infiltration.
Unwary users risk financial peril and shut-down of the company. These threats are worsening as we continue to become a digital society.
That’s why we recommend employers use tailored simulated phishing tests and training to help keep users on alert. They need to stay wary as the criminals only need one click to hold a company to ransom.
How Phishing Can Break the Company
Criminals getting into the company has disastrous outcomes. For example, Munster Technology University has confirmed the cyber-criminal gang BlackCat was behind their ransomware attack earlier this year. The gang encrypted and stole sensitive data before releasing it on the dark web.
Although MTU has not confirmed how this attack happened, ransomware usually works through employees clicking malicious links and failing to recognize the signs of a phish.
More Examples of Real-Life Phishing Emails
Website Content Forms
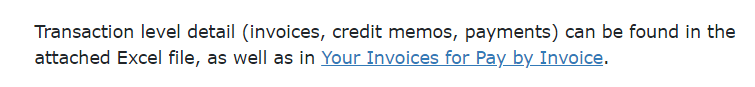
Cyber-criminals have been submitting phishing scams through website contact forms. First, the user is tricked into clicking a link. The emails usually make fake legal threats, and once the user clicks the link, they automatically download a zip file containing IcedID malware. Learn more.
Ring Security Camera Scam
Customers of Ring, a popular home-security camera, have fallen victim to a phishing attack. Cyber-criminals spoofed as Ring manipulated users to enter their credentials in a fake log-in page. After users carried out the action, they were redirected to the real website, making it seem credible. Learn more.
Turkey-Syria Earthquake Phishes
Cybercriminals can take advantage of emotive news articles to create more alarming and urgent phishing emails. Users should be careful not to give donations to unknown users and organizations, or clicking links promising “must-see” or “unseen” news footage. Learn more.
What Steps Can I Take to Keep Down Risk?
By following some easy-to-remember methods of best-practice, users can make more informed decisions about the emails landing in their inbox. Our approach has helped many companies lower their security threat, so here are five steps to help safeguard inboxes and minimize the chance of clicking that link:
- Check the email domain and user are genuine
- Remain wary of emails which try to alarm the user
- Verify and double-check the destination of any links
- Scrutinize any unexpected attachments
- Look for any spelling mistakes or inconsistencies
Let’s get into this in more detail:
Step #1. Check the Username and Email Is Legitimate
Remember that although most emails appear to come from a trustworthy source, cyber-criminals can easily spoof domains. Even worse, criminals can use scraped data bought on the dark web to trick employees. This misuse of personal information, known as spear phishing, tricks employees by making the email seem more real.
Worse still, criminals can make emails appear as though they came from within the organization. Business Email Compromise targets employees with access to sensitive data by mimicking someone of authority. If employees keep social media private and only use their work email for work, the risk of this occurring decreases.
Furthermore, all employees can benefit from being able to report any emails they find suspicious. Newer employees who haven’t learned things like their regular contacts yet should feel they can raise any doubts. This, in combination with simulated phishing attacks, helps minimize risk of disaster.
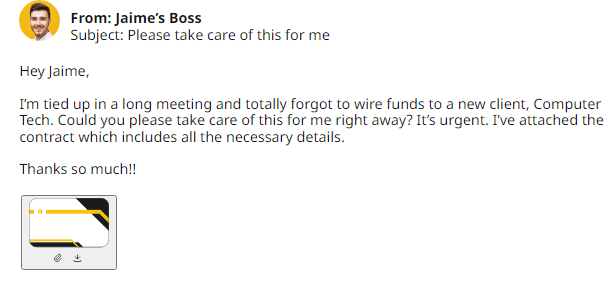
Step #2. Ask If They Are Making You Feel Stressed
Every now and then, we see a phishing email which makes us pause. Be it a password update, a compromised account, or a boss who needs data ASAP, this emotional ploy remains the hacker’s most valuable tool. In combination with a spoofed domain and username, this tactic has a much higher success rate with the poorly-advised employee.
Therefore, team leaders should make employees aware that nobody in the company will make urgent demands for sensitive data. Criminals use these emotional ploys to stop employees from seeing the other tell-signs that they are responding to a phishing email.
By staying calm, particularly by using verbal confirmation and a robust reporting system, employees can minimize risk of a security breach. If another employee needs sensitive data, then communication is key, and everybody should feel comfortable to take heed of best-practice.
Step #3. Investigate What They Are Trying to Make You Click
Although scary, a phishing email by itself is not necessarily dangerous. Its final objective was not to make it into the employee’s inbox, but to get them to click on something malicious. The emotional ploys and spoofing may make for easier giveaway signs, but what about the link itself?
By hovering over any links with the mouse, the employee will see where the link is taking them. They may see a suspicious, shortened link, or that the link leads to a totally different domain. Either way, it is a much safer way to check authenticity, minimizing risk of viruses and ransomware attacks.
Even if the link is hidden behind a button, such as “Manage Subscription”, employees can use the hover technique to see a preview of the URL in the corner. Furthermore, verbal confirmation and reporting will give the employee the final say over any unsolicited emails.
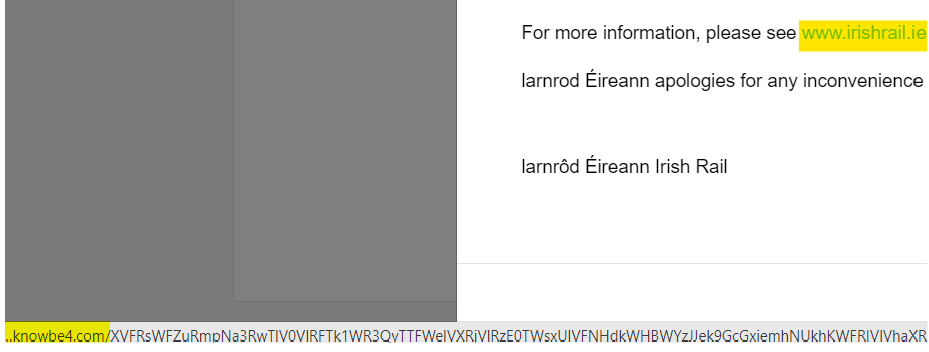
Step #4. Check for any Mistakes
A quick and easy way of finding out a phishing email is by checking for spelling mistakes. That isn’t to say every email with an error is a phish, but general inconsistencies coupled with an inappropriate tone are usually tell-tale signs.
By remaining calm and following best-practice, on a second glance, a well-informed employee will be more likely to notice something off in the sender address or the URL of the landing page. This simple act could save the company thousands and a lot of headaches.
Here is an example of a typical, unsolicited email. The potential victim may be drawn straight away to the Account Suspended subject line, and the information their account will be suspended in 48 hours. But by taking a moment, they could see that although it appears to be from Amazon, it is misspelled:
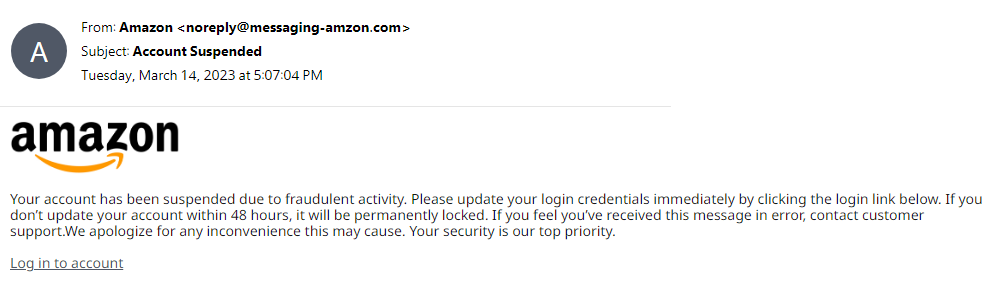
Step #5. Be Careful of Any Unexpected Attachment
Criminals can also trick employees into downloading ransomware or malware. At MTU, the ransomware attack caused, “substantial reputational and financial loss” as investigations continue. Evidently, ransomware continues to be a threat.
Criminals can attach ransomware to the links and documents found in emails, resulting in the system locking out the user. The criminals can then encrypt and mine sensitive data, demanding that the company pays them a fee. They cannot take the criminals’ word they will restore the systems if the company pays.
A huge majority of attacks occur after employees unknowingly give up information to criminals spoofing superiors, and clicking on unsolicited attachments. Verbal confirmation, a robust reporting system, and consistent training on cyber-security best-practice can minimize the threat of ransomware attacks.
Ensure Users Know How To Spot a Phishing Email
Tech Guard provides a Security Awareness and Training program that trains staff on cyber-security best-practice, such as taking heed of GDPR or recognizing signs of a phish. We provide varied but stable training which helps keep cyber-security on the employees’ minds.
Whatever specific needs your company has, Tech Guard can make the best plan suitable to grow security awareness among the team. By putting forward training modules or ‘Phish Alert’ buttons, Tech Guard helps foster a work environment where best-practice remains a priority.
Check the Phish-Prone Percentage of your Company
To find out how phish-prone you or your staff are, take a free phishing test with us to test your IT security, and figure out whether more training is the company’s best line of defense.
Contact us to see how we can minimize the threat of cyber-attacks, ensure employees know how to spot a phishing email, and even help with GDPR compliance.
Frequently Asked Questions
- What is the strongest indicator of a phishing email?
There is no one indicator of a phishing email because the criminal will use multiple methods to manipulate the user into to doing something they wouldn’t normally do. Emotional ploys, pressure to download attachments and impersonations of senior staff can result in a successful attack if the employee is not careful. Constant training is key in decreasing the risk.
- What happens if you open a phishing email?
Getting a user to open an email is half the battle for the cyber-criminal – the user still has to click a link or download something malicious. Still, it is always a good idea to avoid and report anything suspicious immediately to avoid damage being inflicted.
- How do spammers get your email address?
If your email is out there, they can get it. Criminals scrape the internet to find your personal data, resulting in more powerful attacks known as spear phishing. Your email can also be involved in a data breach and put on the dark web, meaning constant vigilance and unique easy-to-remember passwords is a good idea.