By now, many of you that have not been under a rock for the last couple of weeks have heard about the worldwide ransomware cyber-attack WannaCry Decrypt0r that began in earnest on Friday 12th May 2017. The new ransomware caused major disruption to the IT systems of 40 National Health System hospitals across the UK (resulting in most non-emergency operations being suspended). Not only that, but it also caused disruption to an additional 200,000 victims, distributed over at least 150 countries (including several banks, Renault, Nissan, FedEx Corp, Telefonica, German Railways and even the Russian Interior ministry).
How Did This Happen?
Global reports from cyber security experts confirm that this ransomware gets onto a network through an unsuspecting user clicking on a link or attachment in a spam email.
The last few years and countless data breaches have shown that human error (due to a lack of security awareness training) from phishing and social engineering is the number 1 cause of cyber-attacks, ransomware and data breaches worldwide. Unfortunately, many companies including hospitals who have not invested in security awareness training and ongoing testing of their staff with simulated fake emails (to keep them savvy to the latest scams) will continue to be the most vulnerable to this and future similar style cyber- attacks.
Typically, the emails containing WannaCry offer fake invoices, job offers and other incentives. Within some of the emails is a password protected .zip file, so the email can use social engineering to persuade the victim to unlock the attachment with a password and that, once clicked, initiates the WannaCry infection. Infected machines have then six hours to pay the $300 and every few hours thereafter, the ransom goes up.
The worst part of this virus is that it takes advantage of a known SMB vulnerability in the Microsoft Windows operating system, so it is able to spread across the internal network very easily to other machines that have not been patched or updated to protect against this vulnerability. Microsoft released a patch for this back in March this year, however many companies unfortunately do not patch their machines as regularly as they should – a mandatory task which by now is hopefully obvious to everyone that values their business.
The Wall Street Journal created an InfoGraphic to explain how it works.
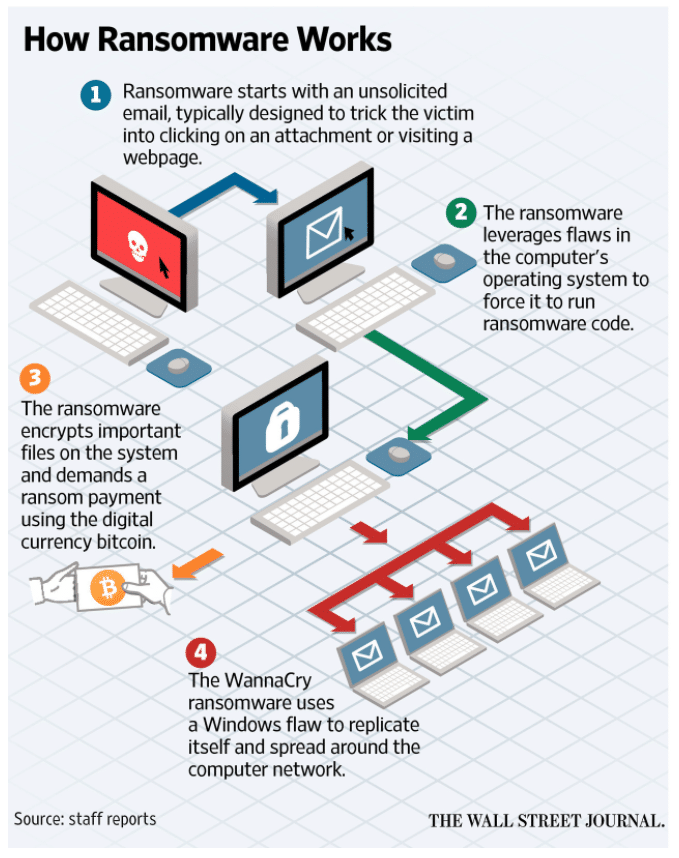
How to prevent WannaCry?
The first step should be to ensure that all your computers and servers have all the very latest critical security updates installed. We cannot stress the importance of the word “all”. Do not just install this critical update and think you are safe.
Unfortunately Microsoft did not explain in clear and simple way (for most non patch-savvy folk) how to correctly ensure your computers are protected. The patches they recommended be installed have now been superseded by other more recent patches, which businesses need to look for. See our download link below for more information on what patches you need to install.
Microsoft also advises companies and users to disable the SMBv1 protocol, as it’s an old and outdated protocol which is already superseded by newer versions, such as SMBv2 and SMBv3.
Download our guide to the latest Microsoft patches that protect against WannaCry ransomware:
What to do if I have been infected?
This strain of ransomware cannot be decrypted. The encryption is of a very high standard and impossible to decrypt unless the coders have made a mistake not found yet. We recommend you recover from backups and if your backups fail or do not exist, try a program like Shadow Explorer to see if your computer has been taking Shadow Volume Copies of your files in the background which you might be able to recover from.
1st Lesson – How to prevent ransomware in the future?
Companies urgently need to re-frame their thinking to IT Security. Instead of relying on all the latest security technology they should being focusing on reducing the largest risk in their organisation – human error!. One click is unfortunately all it takes to bring a business to a grinding halt and the events of the past weeks prove this.
Ongoing Security Awareness Training on the latest scams and testing of staff with regular fake phishing emails simulating the latest scams continues to be the most effective and proven way for companies to reduce their risk of a ransomware cyber attack such as Wannacry; the resulting downtime/data breach it can cause, or indeed any social engineering/phishing style cyber attack.
The introduction of the new EU GDPR (General Data Protection Regulation) on 25 May 2018, which supersedes Irish data protection law, not only mandates security awareness of staff and appropriate security controls around personal/sensitive data, but also introduces hefty fines (up to €20 million) for companies that do not do so and have a data breach. Ransomware could also be deemed as a breach of GPDR as it can affect the access to personal data and can in some cases affect the restoration of data.
It is important to note that any IT Security approach should be a layered one, and while very important, it should not just contain Security Awareness Training and Testing. Unfortunately there is no silver bullet. Any IT security approach should also incorporate regular patching of the latest critical security updates along with a next generation Anti-virus software for all machines, a next generation Firewall protecting your network, Privileged User Access restrictions, DNS protection, Email Attachment Restrictions and a host of other important security controls.
2nd Lesson – How to prepare for when, not if, I’m attacked/hacked? (A Tested Backup and Disaster Recovery Process Is Critical)
This is important. Regardless of what security measures you put in place to help reduce your risk of an attack – you will be attacked or hacked one day, guaranteed, and most likely in the not so distant future.
So, what does one do? Remember the old saying “Those who fail to prepare – prepare to fail”.
The number one thing all businesses need to do above all else is to ensure they prepare for the worst. So when their server or files are hit with ransomware, they can recover that server or their data in the shortest possible time and resume business operations. When ransomware hits – it hits hard and like we seen with the NHS, etc., business operations are halted and customers are turned away until IT systems are recovered, severely damaging that reputation you worked so hard to build up.
In layman’s terms – this means backing up your all your critical data and applications away from your business and not just to a local device. Many ransomware viruses will scan the network or server for attached backup devices and attempt to delete them.
Be sure you have a tried-and-tested backup and disaster recovery process, to not only protect your critical data and servers, but to be able to quickly recover them and continue to serve your customers.
How Tech Guard Can Help?
Here at Tech Guard we provide our client’s with a world class Security Awareness Training and Testing program that we have found to drastically reduce their risk from such attacks. We train their staff on security awareness, the latest scams, and we test them on an ongoing basis with fake emails so they know how to spot a complex phishing attack when the real one hits their inbox.
Trying to assess your risk….wondering how phish prone your staff are? If not – you should be! Get in touch today, we can undertake a phishing security test of your whole organisation.
Tech Guard also provides leading affordable backup and disaster recovery solutions to businesses that allow them to recover their critical IT systems within minutes instead of days keeping them in business.
Contact us for more information or to see how we can help reduce your risk.


— 4 Comments —
Comments are closed.