In May of this year, the world was shook by a global ransomware attack, the now-infamous WannaCry, which is believed to have affected more than 400,000 machines. It shook the world, crippling business big and small across a wide variety of industries. It utilised a vulnerability in the outdated Windows protocol Server Message Block (SMB) v1, and Microsoft even developed a patch for Windows XP to help defend against it. How could such an attack have caught so many organisations off guard? Well, lack of patching, cited the experts, and lack of security awareness on behalf of their employees. Patch your machines now, train your staff, and you’ll be OK going forward. Then, the following month, it happened again – the world was hit by NotPetya, a ransomware strain believed to have infected a further 250,000 machines around the world. It’s worth noting that both attacks managed to affect PCs in Ireland, and that the second of the two major attacks could have been prevented if these companies had taken appropriate measures following WannaCry.

BadRabbit is the latest in a streak of mass-ransomware attacks this year, and may have been unleashed by the creators of NotPetya
As of this week, yet another strain of mass-ransomware is out in the wild, which has been dubbed BadRabbit. While it doesn’t utilise the same vulnerability as the previous two infections, its modus operandi is very similar in that it relies on both the SMB v1 protocol (which is largely defunct in 2017) and heavy use of social engineering to trick employees into clicking their malicious links. It’s an epidemic, and too few companies are learning the lessons that the cyber and business communities have gleaned from these attacks.
BadRabbit first appeared in Russia around the 24th of October and has been spreading like wildfire across both public and private sector networks since then. The attacks have since spread to Ukraine, Turkey, Bulgaria and Germany, and will no doubt reach further afield over the coming days. In particular, it seems to be targeting corporate bodies such as news and media outlets, but has also been found infecting Kiev Airport in Ukraine and other public infrastructure.
As is the case with all malware, BadRabbit doesn’t appear on your computer out of nowhere – it relies on user error in order to infect a machine, and needs to trick regular users into downloading it. It operates as a “drive-by attack”, where victims download a fake installer for Adobe Flash from an infected website. Genuine websites, particularly European news/media sites have been compromised, prompting the user to update Flash to view the content. Once directed to a realistic-looking page, the user is then prompted to download an .exe and install it. This initial file contains no ransomware, and would not be picked up by antivirus software. Only once the user clicks and manually launches this program, allowing it to install, does it download and infect them with ransomware.
Where previous ransomware attacks could be carried out by a user clicking a single link in a phishing email, you can see that BadRabbit has several steps to it, which should (in theory) reduce the numbers of users falling for the ploy. In practice, however, this does not appear to be the case, as many regular users have been granted admin rights to their respective machines or even networks, allowing such malicious software to be installed without the knowledge of their IT departments. Proper access controls and account permissions is just one way in which the spread of malware could be prevented. If a user does not need admin access to their machine, they should not have it. More importantly, the act of providing cyber security awareness training to staff could have taught them how to recognise these fake sites and phishing links, thus preventing them from downloading the file in the first place.
Once BadRabbit is on the system, it acts similarly to NotPetya. While it doesn’t utilise the same EternalBlue vulnerability as its predecessor, it does still take advantage of Windows SMB v1 to spread. It essentially relies on local password dumps in addition to trying a list of all common passwords, in an attempt to spread from one PC on the network to others. While ransomware attacks such as these can equally infect a home or business user, the biggest reason that they affect organisations more is that they can travel at speed across the large networks of PCs. Windows SMB v1 is an old protocol and has been superseded in most cases by SMB v2 and SMB v3, so many companies have opted to disable SMB v1 in the wake of the WannaCry and NotPetya attacks. Many other companies, unfortunately, have not.
At this point, once the ransomware has been installed, it will reboot the infected PC and display its ransom note on the screen. The requested price is 0.05 Bitcoins, equivalent to about €240, per each infected machine. Having said that, there is never any guarantee that these hackers will restore files even after the ransom is paid, as is regularly the case with ransomware. Leading cyber security organisations generally don’t advise paying these ransoms, as security experts believe variations such as NotPetya were aimed for maximum destruction instead of profitability, and very few users were successful in having their files decrypted. While we don’t know for sure, it is suspected that BadRabbit was created by the same authors as NotPetya, which could mean that chances of file recovery are low as well. Unfortunately, in many cases the most costly part of a ransomware attack is not actually paying the ransom, but the downtime to critical systems and loss of sensitive data. Global ransomware costs are estimated to hit €5 billion by the end of the year.
At this stage of the process, how then does a business retrieve their crucial files? They restore their backups, of course. Any sane company nowadays that works digitally will have some means of backup, but not all will work against an attack as aggressive as ransomware. Files synced back to the cloud are often replaced with their encrypted counterparts, and backups have been known to fail or become corrupt and must be regularly tested. Any company that employs the ‘Holy Trinity’ of backups would have local, offsite and cloud copies of their files, with incremental backups taken to allow maximum granularity when recovering. These should also be regularly tested, through screenshot verification and other means, to ensure they will actually work when needed.
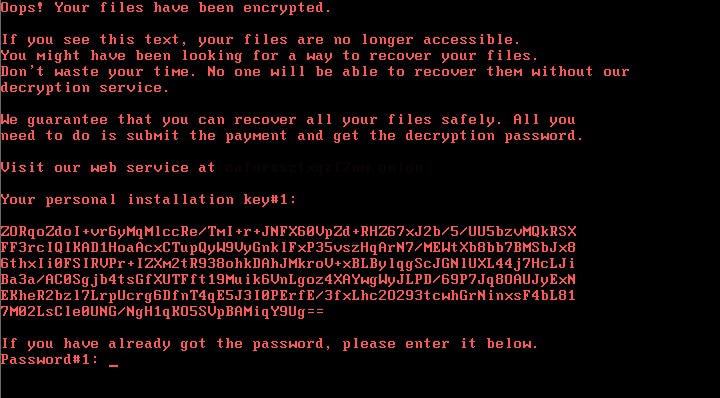
BadRabbit ransomware requests 0.05 BTC per machine (about €240). It is suspected to be an improved version of the NotPetya strain.
With so many organisations falling victim to ransomware, it’s not a surprise that cyber criminals are opting to create newer strains and continually attack computers all over the world. There is so much profit to be made in ransomware, taken from hard-working businesses, that ransomware is even being sold as a service on the dark web. Is there anything that we can do to prevent them from infecting our machines?
The answer is, as always, to take a layered and comprehensive approach to security, and to closely follow best practice in the industry. Regular patching, security awareness training for users, robust and tested backups, admin access controls – these are just some of the steps that any business can and absolutely should take which are quite effective against malicious cyber attacks. However, as security evolves, so does the software used by hackers. This is why we don’t advise implementing just one measure, or to implement measures and just forget about them. Cyber security needs to be applied to every aspect of a network and continuously managed, as your company is only as secure as its weakest link.
While many small to medium businesses may not have the skills or resources in-house to tackle such threats, they are hit just as frequently as larger enterprises. For these companies, we would heartily recommend speaking to a Managed Cyber Security firm – such as Tech Guard. If you’re concerned about BadRabbit or the next strain of aggressive ransomware and how it could affect your business, please speak to us to avail of our free cyber security consultation.
