New research from DataSolutions, an Irish IT solutions provider, has revealed that a majority (60%) of senior IT decision makers consider human error to be the greatest threat facing Irish businesses and organisations at the moment. This is consistent with results of similar surveys in other countries such as the US or UK, as cyber criminals evolve to target end-users and take advantage of improperly-trained staff instead of trying to bypass or hack complex technical security measures. The survey also revealed that 93% of respondents claim that they have a formal cyber security and defense strategy in place to help navigate today’s online threat environment, particularly in a post-GDPR world.
Ticketmaster Ireland Among Those Affected in Huge Third-Party Data Breach
It has come to light that a recent breach disclosed by Ticketmaster UK may be much larger than initially reported, with not just the company’s UK site, but also their sites for Ireland, New Zealand, Australia, Turkey and even the US found to contain digital card-skimming code. Similar to the recent breach at Harvey Norman, this incident was caused by cyber criminals compromising a third-party service provider, not the site itself directly, leading security experts to believe many more websites may be at risk or have been compromised. This is part of a concerning new trend whereby cyber criminals are targeting third-party providers, who may deal with hundreds of websites, rather than attacking a website individually, exponentially increasing the damage inflicted.

Ticketmaster originally believed that only its UK website had been compromised, in a statement released last week
Harvey Norman Among Companies Compromised in Third-Party Data Breach
Harvey Norman, the retail giant with 13 stores in the Republic and a further two stores in Northern Ireland, has admitted to customers that it suffered a data breach through a third-party tool used on its website. “We wish to alert you to a data breach that has occurred in the systems of a third-party website service provider, Typeform, which has resulted in the unauthorised access to some Harvey Norman data,” the company said earlier this week in a statement.

Harvey Norman was just one of the many companies affected by a breach at Typeform, a third-party website service provider
How to Check If Your Business or Personal Email May Have Been Compromised
It’s 2018, and cyber crime is on the rise. It seems every other week there is another data breach or cyber attack somewhere in the world, and many people are rightfully apprehensive that they may be hacked too, or even that their details may have been exposed online through a breach of a service that they use. What if your email and password were compromised in the Adobe breach in 2013, the Yahoo breach in 2016, or the LinkedIn breach in 2012? What if your email had been obtained online and sold to cyber criminals as part of a spam list, such as Exploit.In, or the Anti Public Combo List, both discovered in 2016? If so, you may be at risk of hackers gaining access to your accounts, or even committing identity fraud against you. Luckily, security researcher and Microsoft regional director Troy Hunt has developed a database so that you can check to see if you’ve been compromised – so you can secure your online presence again.
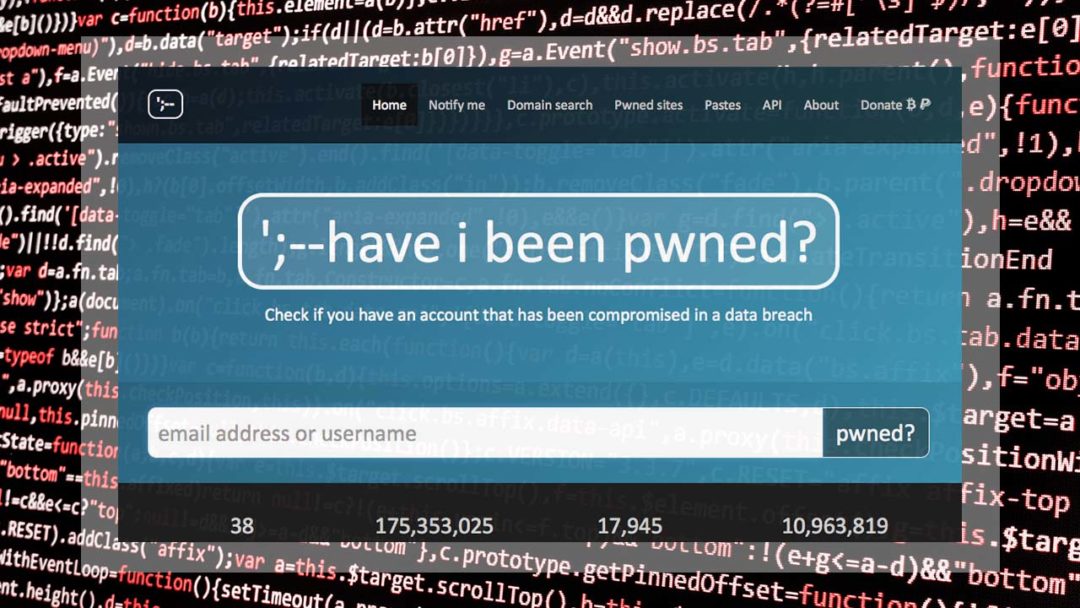
haveibeenpwned.com is a breach database run by security researcher and Microsoft regional director Troy Hunt
EU-US Data Transfer May Be Stopped As Privacy Shield Comes Under Fire
The flow of data between the United States and the EU may be at risk as tensions are rising around Privacy Shield. If you haven’t been living under a rock for the last two years, you will likely have heard of the GDPR – the EU data protection regulation that now fiercely protects EU citizen data, whether in the hands of a non-EU or EU-based organisation. You may have wondered, then, how companies in places like the US are still able to legally hold and process EU data without falling foul of the GDPR, and the answer is Privacy Shield. Privacy Shield is a framework that allows companies on both sides of the Atlantic to transfer data while complying with the GDPR. However, this may all soon change, with Members of the European Parliament calling for Privacy Shield to be brought up to scratch or invalidated.