Ireland is claimed to be wide open to attacks from cyber criminals and rogue states, following an incident in which over 4000 websites around the world were hacked and used to mine crypto-currency. First reported by The Register, the breach affected the Department of Argicultures, Dublin City Council and Fingal, Cork, Wexford and Offaly county councils, and it is suspected to have also affected the websites of the Oireachtas, the Broadcasting Authority of Ireland, Women’s Aid and the Central Remedial Clinic. The crypto-mining attack was not limited to Irish websites, however, as the Information Commisioner’s Office in the UK, the United States courts and many more sites belonging to governments and organisations were also hit.
European Commission Publishes Extra Guidance – Four Months to GDPR
The European Commission has published additional guidance on the upcoming General Data Protection Regulation and how it is expected to affect businesses. The document aims to summarise the purpose and benefits of the GDPR, while also outlining steps that organisations need to take in preparation for the regulation and discussing the steps that the Commission plans to take in the coming months. The European Commission has also taken this opportunity to launch a new online tool to help businesses (particularly small and medium-sized enterprises) meet GDPR compliance in time for the May 25th deadline.

A recent government survey indicates a lack of GDPR awareness among businesses and other organisations
Antivirus Experts Discover Malware Samples Designed to Exploit Meltdown and Spectre
It looks like the Meltdown and Spectre fiasco is only just getting warmed up. Security researchers at antivirus testing firm AV-TEST have discovered more than 130 samples of malware that attempts to leverage the Meltdown and Spectre vulnerabilities. The malware samples analysed by AV-TEST appear to be mostly Poof-of-Concept code, and still in the research phase, however, it is believed that cyber criminals will be similarly experimenting with malware that utilises these vulnerabilities.
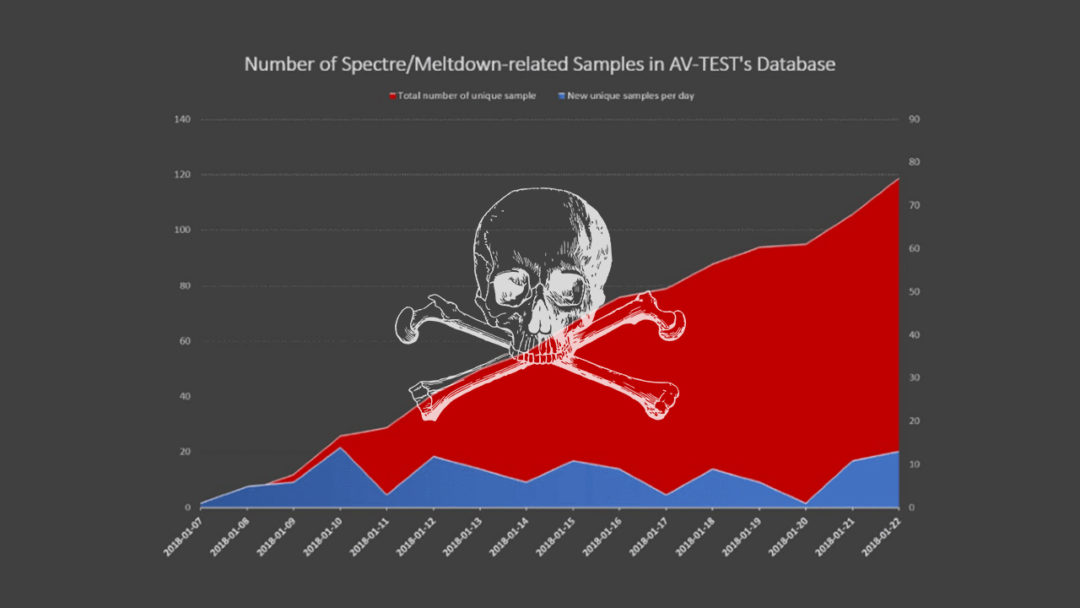
Meltdown and Spectre will haunt IT systems for years to come, potentially, as between them they can affect most processors in use since 1995
Reports Show Cyber Crime Cost Consumers €150bn in 2017
Norton has just released their annual Cyber Security Insights Report, which analyses the effects of cyber crime around the world. One of the key findings of this report is that when it comes to cyber security, “consumers are overconfident in their security prowess, leaving them vulnerable and enabling cyber criminals to up the ante this year, which has resulted in record attacks”. Over the course of 2017, the report estimates that over 978 million adults in 20 countries around the world experienced cyber crime. These attacks cost consumers an estimated €150 billion.
While most people stated that cyber security was important to them, one third of people stored their passwords insecurely and one fifth admitted to using the same password across all sites they use. Over half of the respondents reported either they or someone they knew had been a victim of cyber crime, with the average cyber crime victim spending almost three full working days recovering from the attack.

“When it comes to cyber security, consumers are overconfident in their security prowess, leaving them vulnerable and enabling cyber criminals to up the ante this year, which has resulted in record attacks.”
Carphone Warehouse Fined €450,000 Over Data Breach and “Significant Inadequacies”
Carphone Warehouse have been ordered to pay a fine of £400,000 (over €450,000) to the UK Information Commissioner’s Office, one of the largest fines the ICO has ever issued to a company. A data breach at Carphone Warehouse occurred in 2015, which subsequently led the ICO to investigate the company and discovered a series of “systematic failures” in security practice. The severity of the fine reflected the fact that up to 3 million customers’ data was compromised, in addition to the data of a further 1000 employees. The data itself was also considered extensive by the ICO, as names, addresses, phone numbers, marital status and dates of birth were all leaked. It is further believed that some 18,000 customers had payment card details leaked as well.


