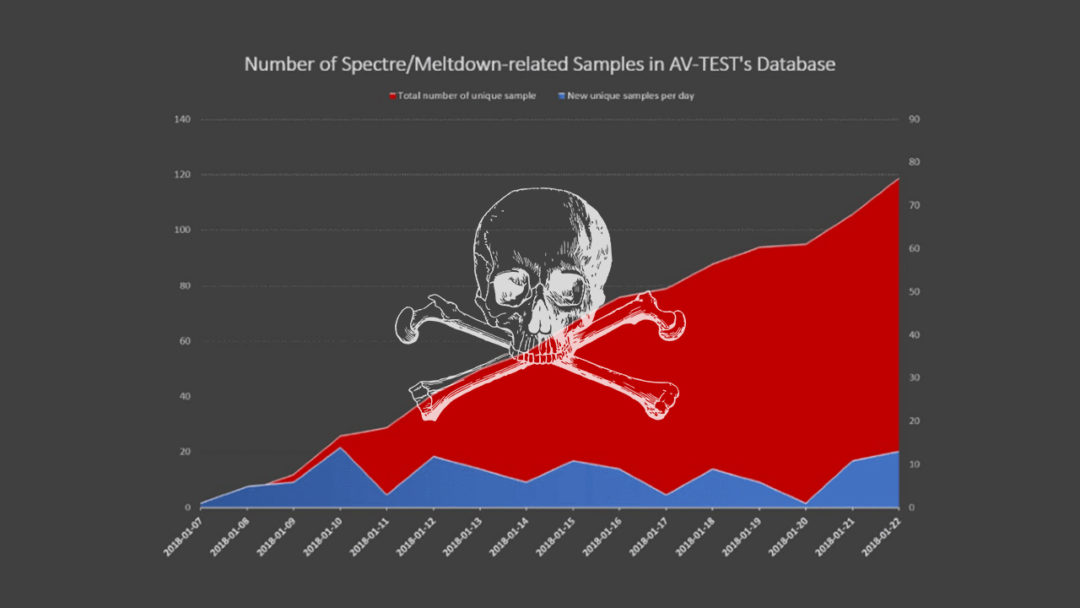
It looks like the Meltdown and Spectre fiasco is only just getting warmed up. Security researchers at antivirus testing firm AV-TEST have discovered more than 130 samples of malware that attempts to leverage the Meltdown and Spectre vulnerabilities. The malware samples analysed by AV-TEST appear to be mostly Poof-of-Concept code, and still in the research phase, however, it is believed that cyber criminals will be similarly experimenting with malware that utilises these vulnerabilities.
Meltdown and Spectre will haunt IT systems for years to come, potentially, as between them they can affect most processors in use since 1995
“Most appear to be recompiled/extended versions of the PoCs – interestingly, for various platforms like Windows, Linux and MacOS,” according to Andreas Marx, CEO of AV-TEST. “We also found the first JavaScript PoC codes for web browsers like IE, Chrome or Firefox in our database now.”
Malware samples started appearing on malware-databases such as VirusTotal almost immediately after Meltdown and Spectre became publicly known. The vast majority of this proof-of-concept code has been uploaded by security researchers, but the rate at which it is developed has lead experts to believe that cyber criminals are attempted to weaponise the code and create malware for use in the wild. Malicious authors of such code wouldn’t upload their malware to virus depositories in order to avoid detection, but it’s only a matter of time before a live sample is found.
Furthermore, it is believed that Meltdown and Spectre attacks may leverage browsers in order to steal data from users. Mozilla have officially confirmed that these CPU flaws can be exploited via web content such as JavaScript, and further proof-of-concepts have backed up these claims.
“Our internal experiments confirm that it is possible to use similar techniques from Web content to read private information between different origins,” said Luke Wagner, a Mozilla Foundation software engineer. Mozilla is also attempting to introduce changes to its Firefox browser which will partially mitigate the risk and make it harder to exploit.
Google, who originally discovered Meltdown and Spectre through their Project Zero team, have also developed mitigations for its own Chrome browser, which was released in late January. It is highly recommended that if you use either browser, you update to the most recent and secure versions.
While Meltdown steals data from the kernel only, Spectre can also steal data handled by other apps. That means any data processed on a computer could be compromised if the malware is in place, including passwords stored in browsers and password managers, emails, business data, photos and more.
In a further development, last week Intel warned that users should stop deploying its current versions of Meltdown and Spectre patches, as people have reported facing issues such as spontaneous reboots and other unpredictable behaviour.
“We have now identified the root cause for Broadwell and Haswell platforms, and made good progress in developing a solution to address it”, said Intel in a press statement. “Over the weekend, we began rolling out an early version of the updated solution to industry partners for testing, and we will make a final release available once that testing has been completed.”
At the moment, that puts users in a potentially awkward situation – the choice between performance and security. Intel, as well as major firmware vendors such as Microsoft, Google and Apple, are all working on potential fixes for the two vulnerabilities. We can only hope that they develop something soon, before hackers begin to take advantage en-masse.
Like most vulnerabilities, businesses are often most susceptible against them, as cyber criminals will target them and combine their malware with code that helps it spread from PC to PC across a network. With the General Data Protection Regulation coming into effects in less than four months, there has been a notable shift in how businesses protect their data. In addition to revenue lost due to downtime associated with being the victim of a cyber attack, they would be further at risk of receiving large fines for not having sufficient protections in place to prevent a data breach.
