The governments of the UK, US, Australia and more have publicly blamed Russia for the NotPetya ransomware attacks, which crippled businesses all over Europe back in June 2017 with a particularly nasty and destructive strain of ransomware. Last Thursday, the White House press secretary Sarah Sanders stated that NotPetya was “a reckless and indiscriminate cyber-attack that will be met with international consequences”, squarely blaming the Russuan Military and the Kremlin for causing billions of dollars’ worth of damage to businesses and states alike. The same day, the British defence secretary Gavin Williamson accused the Russian government of “undermining democracy”, after the attack, which was primarily aimed at the Ukraine, spread uncontrolled throughout Europe and beyond and caused major disruption to commerce and public services.
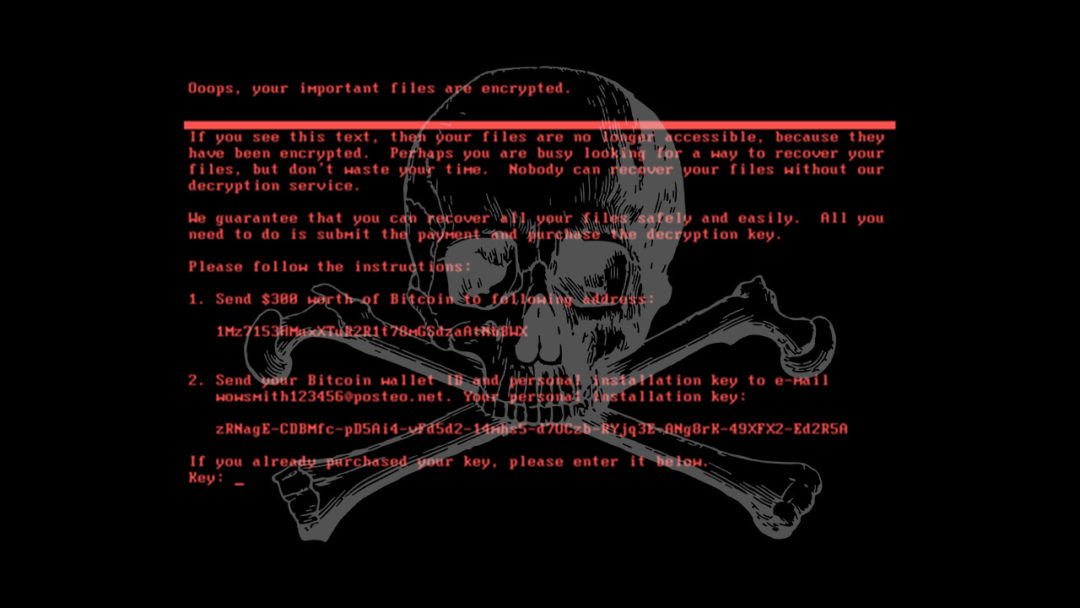
NotPetya has been described as a destructive political move disguised as a normal criminal attack seeking financial gain.
Hours after the US and UK officially put the blame for the devastating attack on Russia, the Australian Minister for Law Enforcement and Cyber Security Angus Taylor also chimed in with a statement.
“The Australian government condemns Russia’s behaviour, which posed grave risks to the global economy, to government operations and services, to business activity and the safety and welfare of individuals”, according to Taylor. “The attack masqueraded as a criminal enterprise but its purpose was principally to disrupt. Primary targets were Ukrainian financial, energy and government sectors. Its indiscriminate design caused it to spread further, affecting other European and Russian business.”
Russia has denied that they were responsible for the attack, which cost businesses an estimated €1 billion. Experts believe that over 2000 NotPetya attacks were launched, directed at Ukraine and spreading outward from there. Among the businesses affected were UK-based Reckitt Benckister (which owns Dettol, Durex and Strepsils), Dutch delivery firm TNT and Danish shipping giant Maersk. Maersk’s Irish offices were among those affected by the ransomware attack, as were the Irish offices of US pharmaceutical company MSD and UK advertising giant WPP, demonstrating that Irish businesses are susceptible to these new political cyber weapons, despite Ireland being far from the firing line of the attack.
Similar to previous mass-ransomware attack WannaCry, NotPetya took advantage of vulnerabilities in the Windows operating system in order to spread between PCs and deliver its deadly payload, encrypting any infected computer and rendering them useless. Early on in the attack, the payment website that NotPetya directed victims to was shut down, ensuring that once encrypted, there was no way back for infected machines.
The most important similarities to note between WannaCry and NotPetya, though, are that both attacks are preventable if proper cyber security practice is carried out. These attacks were particularly effective against businesses and organisations who have multiple PCs on the same network, as it can use an insecure or outdated machine as a doorway to infect the entire network. The main vulnerabilities were patched by Microsoft after WannaCry hit, with Microsoft even releasing a security update for the long-obsolete Windows XP operating system. However, businesses and even government organisations did not take heed following WannaCry and allowed NotPetya to become the most costly and destructive cyber attack that the world has witnessed to date.
How can I protect my business against such malicious cyber attacks?
In addition to regular security patching, other crucial steps that businesses should take to help prevent ransomware attacks in future include using or upgrading to next-generation antivirus and firewalls, having a robust and regularly-tested backup and disaster recovery system in place, and providing staff member with cyber security awareness training. Phishing (malicious scam/spam emails) has been one of the main vectors through which mass-ransomware and other sophisticated malware attacks spread and infect a network.
With the EU’s new General Data Protection Regulation coming into affect on the 25th May of this year, many of the above steps will be written into law as requirements for any business holding or processing EU citizen data, with hefty fines at stake for companies who are not compliant by the time the deadline passes.

— One Comment —
Comments are closed.