What are QR Codes?
QR codes are digital images that when scanned by a smart phone app, allow rapid access to a certain document or website. They are often used for restaurant menus, business cards, links to videos in adverts, access to sporting events etc. They are fast becoming the norm as they help facilitate the move to contactless communications.
QR codes however are quickly becoming another way cybercriminals can trick users into accessing a website or document as it can be more difficult for a user to verify (in advance) the website address, the QR code will take them to.
Cyber attackers however can interfere with QR Codes and lead victims to malicious websites where their financial and personal information is stolen.
QR Code Scams
Some criminals have begun sticking fake QR Codes to parking meters enticing unwitting drivers to scan the code, and hand over their credit/debit card information in the belief they were paying for parking when they the money went straight to the criminals. Earlier this year the FBI published an advisory to warn people.
Many paid and free sites exist that will allow one to create their own QR code allowing bad actors to come up with elaborate attacks or techniques.

This QR Code we generated above allows someone to quickly and easily connect to a Wi-Fi connection. While this is convenient in a shop/restaurant/café, or to provide guests access to your wireless network, it could be very easily abused and used to entice users into connecting to a malicious network.
There are many other types of QR codes and all of these are relatively simple to repurpose for malicious activities.
A recently reported phishing email utilises a QR code while posing as DHL. The criminals behind this scam are exploiting QR codes in a unique way to avoid detection.
A fake DHL themed email begins the attack and although the sender’s address in this scam has nothing to do with the courier service’s name, the message body has a corporate logo, an order number and the purported date of package arrival, all of which are very convincing.
The reported scam notes: An order has arrived at a nearby post office, and the courier was unable to deliver it personally. Normally a link to “resolve the issue” would be included, but this time there is a QR code for the user to scan.
Albeit this scam email below is directed at companies with Spanish employees, the same scam could apply no matter the language or country.
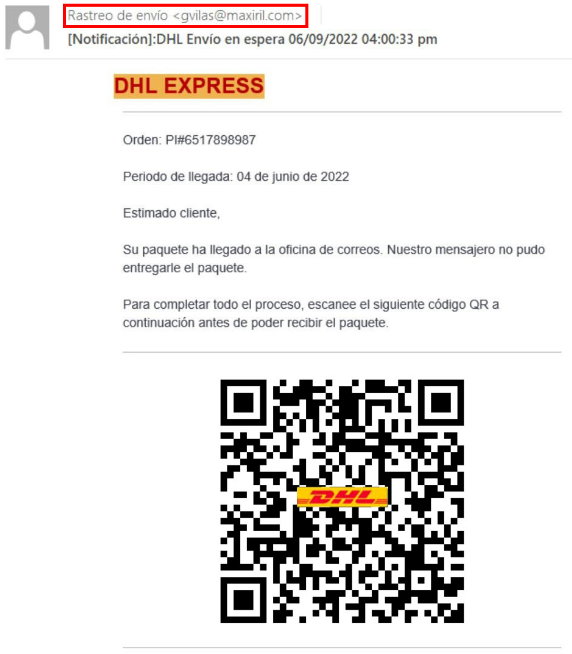
The attackers are counting on the victim using their smartphone to read the QR code. This will cause the malicious website to load on a small screen where the URL is not fully visible and other phishing scam signs are more difficult to identify.
How to thwart an attack?
The best ways to help thwart such attacks is to:
- Always Stop, Look and Think. Are you expecting the email? Does the context indicate an unexpected or unforeseen problem has suddenly arose? Does the email infer a sense of urgency or a negative consequence if not actioned?
- Verify an emails sender address to ensure it is genuine.
- If you need to use a QR Code scanning app, use one that offers a preview where a QR code will take you before it takes you there. If this is not possible or if in doubt, don’t scan the QR Code. It is best practice to instead visit the genuine website via a web browser.
- If you’re expecting a shipment, be sure to make a note of the tracking code and check the status of the shipment on the official website.
- Where possible, save genuine links to work and personal cloud-based services (including courier services) in your PC and phones bookmarks. Access these sites via your bookmarks and avoid clicking links to these services in an email.
If in doubt, before you take any action, understand and follow your company approved policy/procedures for reporting suspicious email activity. The sooner an incident is reported, the sooner measures can be put in place to prevent a breach.
More info:
QR Codes in the Time of Cybercrime (knowbe4.com)
Criminals steal payment details of DHL customers | Kaspersky official blog