Gmail Phishing scams and other email trickery is on the rise using fake attachments to make users more vulnerable to a cyber attack. Learn how to spot them and how to safeguard your business and personal accounts from new phishing scams.

As current events have shown, even the upper echelons of American governance have been vulnerable to phishing scams. The Democratic National Committee’s official email accounts were recently the target of an effective phishing campaign, leaving us all to question the ways in which we’re vulnerable to cyber attacks.
How To Spot Fake Attachment Phishing Scam
A new extremely active phishing technique, aimed at Gmail and other email services, is being implemented to nab log-in credentials that are designed to fool even the most educated digital users.
The scam works by hackers sending out emails via hacked accounts to those users’ contact lists. Many of the emails include an image that looks like it could be an attachment, though when the image is clicked on, instead of a preview of the file, a new tab opens with a mock prompt from Gmail to sign into the email account again.
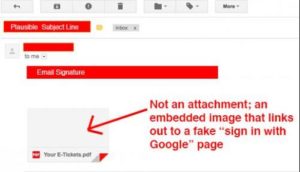
Gmail Fake Attachment (Appears as an Image)
Even the URL mimics an actual Gmail page: accounts.google.com. The sign in appears to be perfectly legitimate, though once a user signs on, they compromise their email account and with it other sensitive personal information. Hackers are then able to spread the scam immediately to others in your contact list with the access to your email.
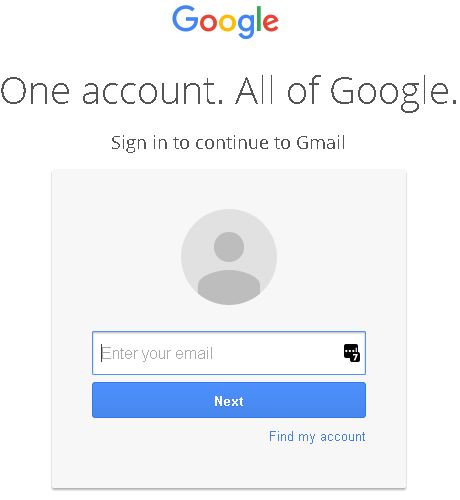
Fake (But Very Real Looking) Gmail Sign In Page
To protect yourself from such attacks you have to change what you’ve always known in regards to cross checking phony-seeming links and emails. As this phishing scam mimics the URL of an actual, reputable website, you can’t always double check by just looking at the link. If you see the following text before the https beginning of the URL: data: text/HTML, this signifies a scam link.

Look out for the URL – keep an eye – data:text before the https is a scam.
As a rule of thumb whenever you log-in to an email service website, or any site asking for credentials, be sure to check the browser location bar and corroborate both the protocol and the hostname for legitimacy. For a Gmail account, it should read like this: https://accounts.google.com/ServiceLogin?… Verify that there isn’t additional text between the hostname “accounts.google.com” aside from “https://” and the lock symbol on the location bar, which should appear as green if you’re safe, as Google relies on this function to signify a secure site.
What Else Can I Do To Protect Myself
Also, consider enabling two-step or two-factor authentication on your email service. This makes it harder for hackers to sign-in to your account even if they have your password.
If you’re unsure of whether your email account may have been the subject of a phishing scam in the past, it’s a good idea to change your password anyway. A function on Gmail allows you to see log-in activity to find out if any other users have been logging into your account without your knowledge. This can be accessed through Gmail’s support page, view the Details icon at the bottom of your inbox. If you uncover any log-ins from places where you haven’t been or any active sessions from undetermined sources you can actively remove those sessions.
Raising your awareness of this issue and staying vigilant on good digital practices can help to ensure the safety and security of your email accounts and personal data.
Remember! Implementing an ongoing and continuously updated cyber security awareness training programme for your staff along with simulated phishing campaigns is the #1 way to reduce cyber attacks in the workplace and keep staff on their toes, aware of the latest scams and threats. Contact us to find out more.
