Recently, car insurance and breakdown cover provider AA faced accusations of covering up the severity of a data breach that occurred in April of this year. The AA, through their customer support Twitter, chose to downplay reports of the breach and assured users that no credit card or other sensitive data had been exposed. Data was leaked from their online shop due to a server misconfiguration. However, this server contained data on over 100,000 AA customers, and included partial credit card data. Despite knowing about this breach for over two months, it wasn’t until the cyber security community cried out in outrage that AA eventually admitted to the severity of the breach. No customers were notified by the AA directly.

No customers that were impacted were directly notified by the AA, despite the breach being discovered in April.
According to a statement made by the AA on July 3rd, “The AA Shop data issue is now fixed, No Credit Card info was compromised & an independent investigation is under way. We’re sorry”. Security researchers, including Troy Hunt, Microsoft Regional Director for the Asia Pacific region, were quick to point out that this was not the case, and partial credit card data had clearly been exposed. While full credit card numbers had not been leaked, the breach did contain the last 4 digits of credit card numbers, in addition to expiry dates and other information that could be used to conduct identity fraud.
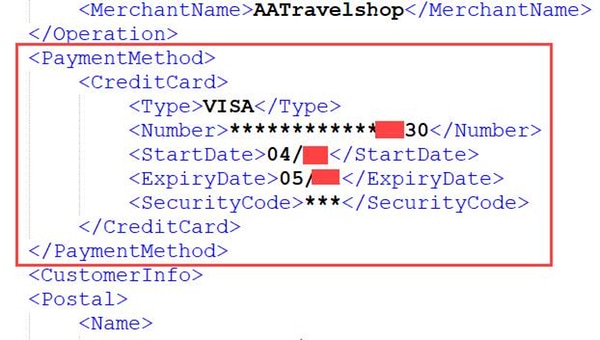
Partial credit card details, exposed during AA data breach.
This of course drew out a more carefully measured response from the AA, as they finally made a full statement acknowledging that names, addresses, phone numbers, email addresses and (in some cases) partial credit card data and encrypted passwords had been exposed. “We are aware of concerns that we fell short in our handling of reports that some personal data from the AA Shop on-line had been compromised. We accept the criticism that the issue should have been handled better. We are grateful for the support of the information security community in flagging issues to us”, according to their statement.
Data breaches under the GDPR
Unfortunately, it’s not only the AA who still attempt to cover up their data breaches. Indian telecoms giant Jio suffered a breach which resulted in over 120 million customers’ data being put up for sale on the dark web. Their official statement reads “We want to assure our subscribers that their data is safe and maintained with highest security”. While there has been no definitive confirmation that Jio suffered a breach of yet, a Reddit has already popped up with many Indian users confirming the authenticity of the data that had been breached. This alarming trend of denying breach incidents until all plausible deniability is gone can be seen in businesses around the globe, as many fear not only the financial repercussions of a data breach, but also the reputational damages. A few months earlier, software vendor Regpack suffered a data breach which lost 324,000 payment records (including credit card CVVs). Their initial statement read “we have run the full security protocol implemented in these cases and conclusively determined that our servers were not involved”. Again, security researchers including the likes of Troy Hunt were hot on their tail, which resulted in a very different statement being released less than two days later; “We identified that a human error caused those decrypted files to be exposed to a public facing server and this was the source of the data loss”.
There are more examples, but what is most concerning at the moment is how these breaches would be dealt with under the upcoming EU data protection regulation, the GDPR. The new laws specifically state that all data breaches must be reported to the relevant authorities within 72 hours, in addition to notifying any affected users. The fines under the GDPR are substantially larger too, with the maximum fine at €20 million or 4% gross turnover, whichever is larger. Data protection laws are being sharply redesigned to give back data control to the consumer, placing more responsibility on any data-controlling organisations to “implement appropriate technical and organisational measures” around data security.
Needless to say, no company wants to be in the position of trying to survive a data breach under the GDPR. Luckily, the GDPR documentation specifies certain controls that it believes are essential in preventing data breaches, and had said that companies who adhere to them will have a reduced chance of being handed down a fine or substantial monetary penalty. These GDPR-mandated measures include practices such as making sure your backup solution is regularly tested, so that customer data may be restored in the event of a breach, and providing staff that may have access to sensitive data (ie. almost everyone) with data and cyber security training.
We’re sure we will see more cases like the AA over the coming months, but by now the majority of companies are realising that data protection law is changing, and the time to meet compliance is now, not after the GDPR comes into effect. The more controls in place and best practices implemented within your organisation, the lower the chance of a data breach occurring, and the smaller the fine handed down in the event one should occur anyway.
